Security + Storage in One
Protect against cyber threats and cut storage costs with software-defined cyberstorage

Slash your storage footprint
Never negotiate with hackers


Recover from any event
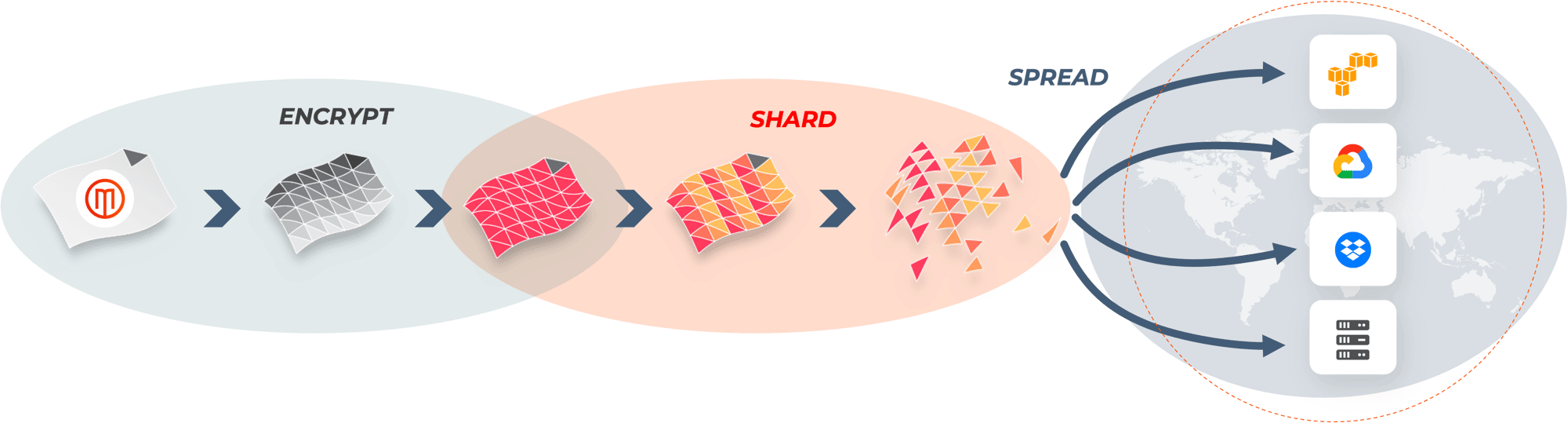
Encrypt, Shard, and Spread Your Data Across Multiple Storage Locations Automatically
Instantly achieve Zero Trust Data Resilience and 3-2-1-1 Protection
Learn how Myota works:
Zero-Knowledge Encryption
Combines practical and quantum-proof encryption for unmatched security.

Shard-Based
Separation
Creates secure, unusable shards of 'digital sand' that are 50% smaller than your original data.
Zero-Knowledge Spread
Automatically distribute shards across multiple storage locations without the traditional overhead.
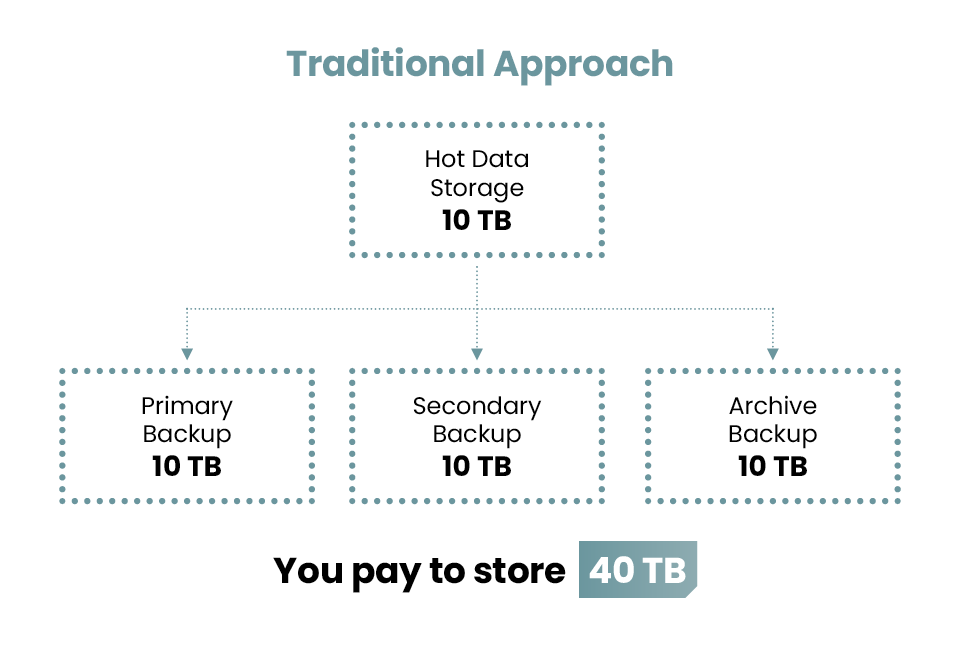
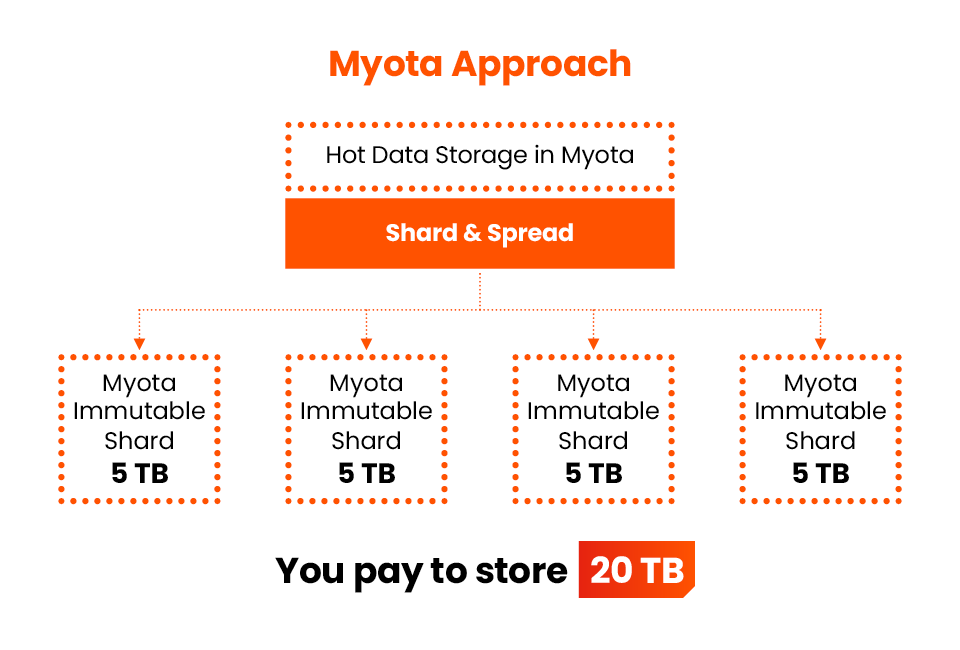
Stop Overpaying for Storage
Traditional backup approaches force you to store several complete copies of your data. Myota doesn't.
-
*10TB backup size shown for illustration. Your actual backup size may vary, but the 50% storage reduction remains consistent.
Myota Integrates with Your Existing Infrastructure to Protect Data Everywhere
Myota User Testimonials

"Myota gives me the ability to copy and protect my data against ransomware, deletion, or loss, acting as a data recovery solution by being multiple places at once"

Sun Capital

"Myota is cutting edge, simple in a good way, and easy to deploy quickly. You don't need to be a tech leader to administer it, so you can delegate that task to others on your team"

Clutch
Recommended Reading
Myota's latest insights and strategies on data security, cyberstorage and ransomware protection.

Critical Veeam Flaws Allow Immutable Backup Compromise

Beyond AWS Credentials: Why the Codefinger Attack Changes Cloud Storage Security